QUESTION ONE
a) Explain each of the following terms as used in computers. i)Wikis ii)Blog – Click here to view the Answers
b) Sawa Company Ltd. are experiencing internal hacking of their computer system.Outline four possible root causes of the problem. – Click here to view the Answers
c) i) Outline two benefits of embracing ICT in learning – Click here to view the Answers
ii) Distinguish between stress and fatigue – Click here to view the Answers
d) i) Define the term lease as used in computer acquisition – Click here to view the Answers
ii) Keziah was selected as chairperson for an ICT committee in her company. Outline four communication skills that she could use during meetings. – Click here to view the Answers
QUESTION TWO
a) Outline four types of computer mice – Click here to view the Answers
b) i) Ergonomics awareness education should address all the safety needs of An organization. Outline four objectives of such an awareness initiative. – Click here to view the Answers
ii) Daisy-Winds Company Ltd. Intends to embrace ergonomics standards in its computer facilities. Outline four benefits that the company could realize from this decision – Click here to view the Answers
c) i) With the aid of diagrams in each case, explain two categories of computer networks based on how information is shared – Click here to view the Answers
ii) Explain two circumstances that could necessitate the use of hybrid topology in a computer network – Click here to view the Answers
QUESTION THREE
(a) Differentiate between microcomputer and minicomputer. – Click here to view the Answers
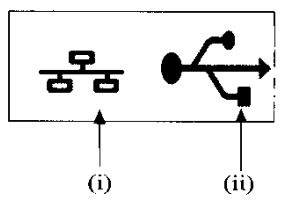
ii) Figure 1 shows typical port signs that could be found in a computer system. Outline the function of each of the port signs labeled (i) and (ii) – Click here to view the Answers
c) Tash was invited to give a lecture on the use of ICT at a conference in a college. Assume she consulted you, outline six qualities of a good public speaker that you could have suggested to her. – Click here to view the Answers
d) Salome noted that a good number of her friends were using pirated software. Explain three categories of risks that are likely to affect their computers. – Click here to view the Answers
QUESTION FOUR
a) Outline three measures that could be used in an organization to mitigate conflict of interest with its staff. – Click here to view the Answers
b) Explain three advantages of embracing ICT ethics in organizations. – Click here to view the Answers
c) i) Outline two challenges of computers at home – Click here to view the Answers
ii) Magnetic disks are popular computer storage medium. Outline three advantages of this storage medium. – Click here to view the Answers
d) Norah was required to describe the categories of computer keys in an examination. Describe three categories that she was likely to mention – Click here to view the Answers
QUESTION FIVE
a) i) Outline three examples of scanners that can be used with computers – Click here to view the Answers
ii) Distinguish between RAM and ROM as used in computers – Click here to view the Answers
b) Explain three benefits that an organization could realize by embracing green computing. – Click here to view the Answers
c) i) Outline three reasons that could necessitate organizations to initiate social responsibility projects. – Click here to view the Answers
ii) A lecturer intends to install a computer software. Explain two categories of software that he could install. – Click here to view the Answers
QUESTION SIX
a) Explain each of the following types of computers: i)analog; ii)hybrid – Click here to view the Answers
b) Differentiate between computer systems implementer and computer systems analyst. – Click here to view the Answers
c) With the aid of a diagram, describe the functional components of a system unit. – Click here to view the Answers
d) i) Jorum was seeking advice from his friend on how to manage work conflict. Outline four measures of managing work conflict that he is likely to have been advised. – Click here to view the Answers
ii) Nancy was required to identify functions of an operating system during a job interview. Outline four functions that she could have identified. – Click here to view the Answers
QUESTION SEVEN
a) i) Explain each of the following terms as used in hardware Acquisition: i) a warranty; ii)interoperability. – Click here to view the Answers
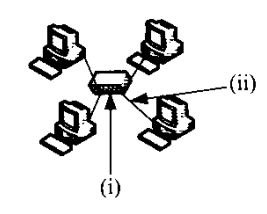
b) Figure2 shows a typical network topology. Outline the components labeled (i) and (ii). – Click here to view the Answers
c) Paul was required to formulate computer laboratory safety rules. Outline four rules that he was likely to list – Click here to view the Answers
d) i) All computers utilize several types of buses for efficient system Communication. Describe two typical categories of buses found in computers. – Click here to view the Answers
ii) Polly, an intern student in a certain college was required to install certain software in all computers in the college. Outline four methods of installation that she could have used. – Click here to view the Answers
QUESTION EIGHT
a) i) List four recordable version of digital versatile disk (DVD) that could be found in computers. – Click here to view the Answers
ii) Differentiate between preventive and reactive conflict management techniques. – Click here to view the Answers
b) Explain two objectives of computer safety policy in organizations. – Click here to view the Answers
c) Communication software is considered as a vital tool in business. Outline four Categories of such software that could be found in business firms. – Click here to view the Answers
d) i) Data privacy is critical part of information communication technology. Outline three measures that an organization could use to realize its data privacy standards. – Click here to view the Answers
ii) Facebook has connected the world as one big community. Outline three negative impacts that are likely to be associated with its adoption by students. – Click here to view the Answers
